How the Federal Government Shutdown is Affecting National Security
Founder’s Note
Welcom e back to Bits N’ Bytes Cybersecurity Education for the new year! We are so thrilled to be rolling out an array of new changes in this coming year, and are all busy getting our heads into the details of planning our strategic operations. With this note, we start off the year with a discussion surrounding the current government shutdown occurring in the United States, bringing on our head policy writer to discuss the impacts on national cybersecurity. The impact on our personal lives is pervasive and imperative, and deserves its due diligence for care and attention. This is why we have created a detailed article for you below, pushing this piece through ideation, editing, and publishing all in the span of 1 week (Much thanks to Google Doc’s fantastic collaborative settings)! As always, here is your reminder that our articles, crafted for ages 5-95, are meant for learning and sharing. We package and publish them for all readers to truly understand their role in the national scheme of cybersecurity and privacy. A stronger democracy starts with awareness, which starts at your dinner table, with your child…talking about national security with the government shutdown. Let’s begin!
e back to Bits N’ Bytes Cybersecurity Education for the new year! We are so thrilled to be rolling out an array of new changes in this coming year, and are all busy getting our heads into the details of planning our strategic operations. With this note, we start off the year with a discussion surrounding the current government shutdown occurring in the United States, bringing on our head policy writer to discuss the impacts on national cybersecurity. The impact on our personal lives is pervasive and imperative, and deserves its due diligence for care and attention. This is why we have created a detailed article for you below, pushing this piece through ideation, editing, and publishing all in the span of 1 week (Much thanks to Google Doc’s fantastic collaborative settings)! As always, here is your reminder that our articles, crafted for ages 5-95, are meant for learning and sharing. We package and publish them for all readers to truly understand their role in the national scheme of cybersecurity and privacy. A stronger democracy starts with awareness, which starts at your dinner table, with your child…talking about national security with the government shutdown. Let’s begin!
How the Federal Government Shutdown is Affecting National Security
What’s happening?
At midnight EST on December 22, 2018, President Donald J. Trump shut down the federal government due to a dispute about his proposed wall along the United States-Mexico border. Since then, it has been more than a month, making this the longest government shutdown in the history of the United States. It began when President Trump asked Congress to pass legislation authorizing a budget of $5.7 billion to built the border wall. The House of Representatives opposed the request and continues to stand behind their decision, creating a standoff between the executive branch, which is controlled by Republicans, and the legislative branch, which is controlled by a Democratic majority.

Source: ABC News
Why Does This Matter?
In the 33 days since the shutdown began, 800,000 federal workers are going without pay, with just over half continuing to work. Many of those who are still working have applied for part-time jobs to make ends meet, and many others are beginning to resign or seek unemployment benefits. Shops and restaurants near Washington D.C. have shut down, as have NASA laboratories and National Park Service sites. Although federal courts are currently up and running, they too are running out of money reserves, resulting in severe amounts of delays in civil cases and court-appointed attorneys working overtime without pay.
Each day that the shutdown continues, the state of the nation’s federal agencies worsens. In fact, it has only recently become apparent that the shutdown is having many unintended and previously unknown consequences, with a risk to national security as one of them. Let’s examine the many ways in which national cybersecurity is being affected as an indirect result of this government shutdown.
1. Limited Staff Personnel in Government Cybersecurity Agencies
National security agencies have not been immune in the dramatic reduction of federal employees due to the lack of pay in the last month. Recent reports say that around 50% of the employees at the Cybersecurity Infrastructure Security Agency (CISA) have taken a leave of absence. CISA, which was created only recently as a specialized department with the Department of Homeland Security in order to more directly address cybersecurity specifically, has run out of funding entirely, as of January 3, 2019, with no knowledge of when that funding will be returned. Similarly, the National Institute of Standards and Technology (NIST), which leads the National Initiative for Cybersecurity Education (NICE), is also working with a staff that is reduced to almost half of what it was before the shutdown.

Source: CNBC
National security threats, however, aren’t stopping because of a lack of security personnel defending the United States. Addressing these threats requires cybersecurity agencies to be operating with a full staff and full use of resources. Otherwise, with this current shortage, we risk not having enough hands on deck to detect and prevent possible security breaches.
2. NIST’s Cybersecurity Guides are Inaccessible
The website of the National Institute of Standards and Technology (NIST) is responsible for providing a gold-standard cybersecurity framework for constructing security measures, along with a portfolio of other standards and practices for both the public and private sectors of cybersecurity. Security leaders were caught off guard by the lack of access to these resources, which became evident when security personnel visited NIST’s website, only to be presented with a message that the site, including all cybersecurity documentation, had not been updated since December 22, 2018, due to a lack of government funding.
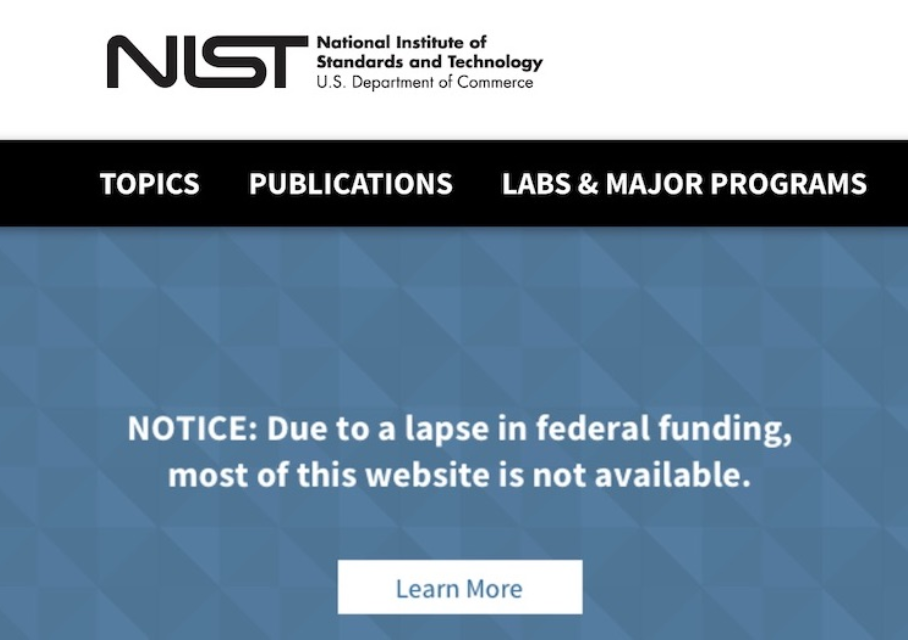
Source: Prilock Security Awareness
The private technological sector primarily uses NIST’s cybersecurity standards as an architectural plan for their organization’s security program. Some of the services NIST provides in its portfolio include recommendations on the best security tools and guidelines for how security technologies, such is encryption schemes, should be properly implemented. Without this documentation, which ensures a high level of security protocol and offers standardized methods of enforcing that protocol, several major technological companies lose the ability to develop and execute rigorous security measures.
The greatest user of NIST’s software in the public sector is the United States government itself, meaning that as long as NIST remains without funding or staff, the government’s cybersecurity measures can not be updated and revisited because federal agencies have no access to NIST’s publications. This unseen consequence may perhaps be one of the largest issues facing the country until the shutdown ends.
3. Lack of Funding for Cyber Investigations
Perhaps less surprisingly, along with a reduction in security personnel comes a reduction in funding for cybersecurity agencies, such as the Federal Bureau of Investigation (FBI), which is responsible for combating many things, including cyber attacks. With dwindling funds across the bureau, the FBI has begun to table investigations into security breaches or cyber attacks, as all resources go to top priorities such as terrorism and counterintelligence. Furthermore, cyber investigations are becoming harder and harder to conduct, due to the expense that is often associated with cyber operations.

Source: MarketWatch
For example, many of these operations rely on digital evidence obtained from Internet service providers and other tech companies with the help of a court order. With federal courts in the state they are currently in, the FBI has begun having difficulty getting orders through to retrieve information. Even when court orders can be obtained, the bureau is still responsible for compensating tech companies for the information obtained, which is next to impossible with the lack of funding. This has resulted in the FBI tabling numerous cyber investigations, increasing the risk of a cyber attack that could go undetected and further threaten national security.
4. Backlog of Security Threats
As the shutdown continues, several maintenance issues start building up. One report found that Transport Layer Security (TLS) certificates for at least 130 United States government websites have expired. These certificates ensure that all security measures for government websites are up to standard, and even when the shutdown ends, there will be an immense a backlog of websites that need updating, creating a heightened risk that something may be missed.
Security personnel in the government also face hundreds of potential threats every single day. These files and threat alerts have not been reviewed since the shutdown began, and when the government fully reopens there will be an immense load of files that must be reviewed, with new ones coming in all the time. Security agents may very possibly prioritize more recent files over older ones, and some of the older files may never get reviewed at all, simply due to a lack of time.
However, some of these overlooked alerts may actually show suspicious activity, such as infiltration of a federal network by a foreign source. If this was the case, cyber attackers could be on a government network for several weeks without detection, giving them plenty of time to infiltrate other defense mechanisms and install malware or security backdoors to give them future access. The longer we go without a security staff actively reviewing threats, the greater chance we have of being hacked.

Source: EfficientGov
5. Weakened Security Due to Password Resets Afterward
Password resets are another example of a security issue that may arise after the government shutdown ends. After a month long unemployment period, many of those 800,000 federal employees will likely either want to or be required to reset their passwords to access government websites. Information technology will have to deal with thousands of requests, and in order to do so, may make exceptions to password management policies, allowing employees to create non-secure passwords in order to expedite the process. More relaxed password policies could open up the government and leave us vulnerable to cyber attackers, who may leverage weak employee passwords.

Source: The New York Times
6. Time Needed to Resume Operations Creates Vulnerability to Attackers
In a previous government shutdown, which occurred in October 2014, federal agencies reported that it was months before they were able to process cases and requests at a normal speed again. The longer the shutdown, the longer the recovery, meaning that it could take several months to recover from the impacts on cybersecurity from this shutdown. The more time that it takes to recover, the more vulnerable the government is to infiltration, as it would be operating without full use of resources for an extended period of time.
As with all these other crises, however, cyber attackers will not hesitate to look for weak spots in the United State’s defence, and federal agencies will have to work overtime the first few months after the shutdown to maintain and actively prevent breaches in their security network, as well as investigate cases occurring during the shutdown.

Source: The New York Post
7. Hiring Crisis for Future Federal Cybersecurity Positions
The longest lasting effect that national security will face is the lack of morale and trust in the government from both employees and citizens. Before the shutdown, government jobs were seen as some of the most stable in the nation, but with 800,000 federal employees out of work, the perception of a government job has changed, bringing with it a decline in workplace morale. This has the potential to permanently impair the government’s ability to recruit talent in the cybersecurity industry, as well as a civilian’s general trust in the cybersecurity of the country.

Source: MSN
Many employees who are currently working in the government have been turning to private work as well, according to a recent report. Without adequate funding or a consistent paycheck, it has been made more and more difficult for federal employees to intercept and mitigate threats to our cybersecurity infrastructure. If current employees continue to leave, new graduates will be deterred from entering the public workforce, causing a recruiting crisis and many empty government seats and federal security agencies in coming years.
So What Now?
The impact of the government shutdown on cybersecurity, though not headlining news cycles, is posing a critical threat to the United States’ ability to investigate, mitigate, and manage security operations. Hopefully, keeping these potential negative outcomes in mind will result in an end to the government shutdown and a speedy restoration to national security. One thing is for sure: if the shutdown continues, without changes to funding, software access to guidelines, or staff, national security will be put at a greater risk every day.
However, even amidst all the chaos, there is a bright spot. Many federal workers have banded together and still continue to work, even without pay. The Committee Chair of the Department of Homeland Security (DHS) recently released a statement, saying that 87% of DHS are still working, regardless of the uncertainty of how much or when they will be paid next. With such dedicated federal employees, we are much more likely to have a smoother transition when the government fully reopens, restoring national security and the nation’s confidence in the United States government.

Source: TIME Magazine
What Can YOU Do?
While many of these overarching cybersecurity threats are outside the hands of the average consumer, there are still steps anyone can take to protect themselves from cyber attacks, and strengthen our collective communal security from attack. To start with, ensure that all personal accounts are secured with a strong passphrase that is changed regularly (and after a data breach) in order to guarantee constant security. Another key action point is to set up multi-factor authentication on as many accounts as offered, on banking, insurance, work accounts and more.* Multi-factor authentication requires a secondary degree of confirmation beyond entering the correct password, such as a code sent through text-message or voicemail to your cell. Along with the correct password, a personal device is required to input a secure code, adding another layer of security to your account and preventing remote access.
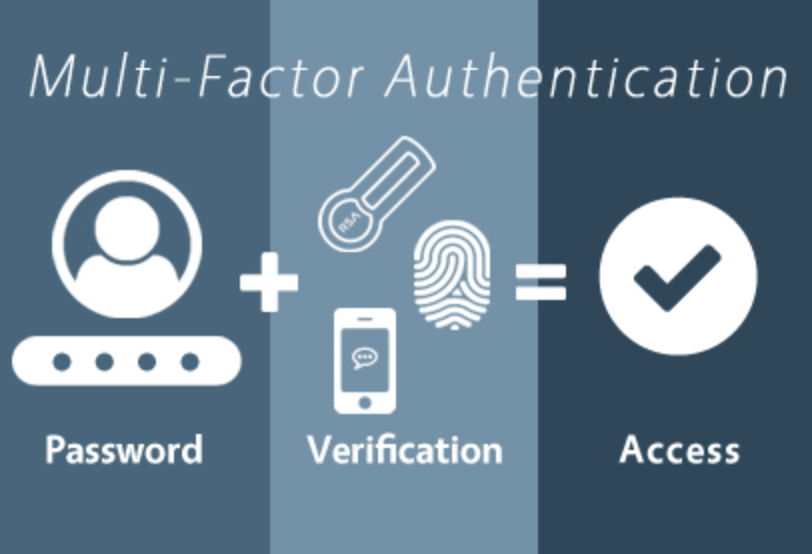
Source: Avatier
When accessing websites and downloading files, especially during the government shutdown period, heed all security warnings before attempting to do so. Currently, websites are not being monitored by the government, nor will they be until the shutdown ends, so extra caution will be required before downloading or accessing foreign files. Do not try to bypass browser safety warnings, as those are solely for consumer security.
No matter which direction this shutdown goes, always exercise reasonable caution when using the Internet. Many personal cybersecurity breaches can be prevented with just a little action from consumers so make smart decisions, password protect your information, and stay safe!
*Check out https://twofactorauth.org/ to find which websites/services offer two-factor authentication!
As always, have a safe and secure week!
Sincerely,
Policy Panther
Policy Panther: Annika Agrawal
 Annika Agrawal is a senior at Hinsdale Central this year and an incoming freshman at Duke University. Her favorite activity is journalism, and she is the incumbent Managing Editor of her school’s news magazine, having a longstanding passion for policy on Capitol Hill. She is also on the literary editing board of the art and literary magazine at school and enjoys writing and editing for local papers in her town. Her friends would say that she is never one to back down from a challenge and that she loves helping people out, whether it’s coaching kids, talking to a friend, or volunteering to play piano for elderly residents. Besides organizing TEDxYouth@Hinsdale, or participating in Science and Math Olympiad, she spends the most of her days holed up in a biochemistry lab, analyzing proteins and hoping to further her research on probiotics.
Annika Agrawal is a senior at Hinsdale Central this year and an incoming freshman at Duke University. Her favorite activity is journalism, and she is the incumbent Managing Editor of her school’s news magazine, having a longstanding passion for policy on Capitol Hill. She is also on the literary editing board of the art and literary magazine at school and enjoys writing and editing for local papers in her town. Her friends would say that she is never one to back down from a challenge and that she loves helping people out, whether it’s coaching kids, talking to a friend, or volunteering to play piano for elderly residents. Besides organizing TEDxYouth@Hinsdale, or participating in Science and Math Olympiad, she spends the most of her days holed up in a biochemistry lab, analyzing proteins and hoping to further her research on probiotics.